Nima's notes

The economics of identity systems
Economists have a unique way of observing and evaluating human activities based on produced economic surplus. Although excessive reliance on this viewpoint can prove myopic and amoral, it is nevertheless a useful tool for assessing the underlying reality of things.
In this article we focus on a detailed understanding of the economic realities of identity systems, in terms of their contribution to value creation, their usage of specific processes, artifacts, and tools, and their relation to the most common economic activities. This will help us understand how and why such systems have become ubiquitous, as well as provide us with a framework to approach future-facing identity system solutions.
Summary
We start by enumerating common categories of activities and usage patterns across different identity systems. Organizing categories of activities by verbs, groups, and stages, may seem like an arbitrary exercise, but it goes to the root of why and how such economic activities have been sustainably occurring in human history, and have been consistently creating surplus. It also helps explain investments in large-scale infrastructure systems such as national identity systems. Additionally, going through this exercise produces the key insight that fundamental improvements to these systems can have the potential to disrupt and improve human activities at scale.
One can generally organize human activities into a hierarchic structure that points to value creation at its apex (see figure below). The other 3 stages or layers to this hierarchy, namely: establishment, preparation, and action, consist of so called supporting activities. The Security administration category of activities can span all these stages, while other categories of supporting activities such as identification, connection, interaction and transaction generally fit within a specific stage.
A significant subgroup of support activities fall within the identity domain meaning they are facilitated by large scale identity systems such as state drivers license programs. Such systems are always accompanied by a set of artifacts such as identification cards or other documents, meant to be used by everyday people as common tools.
In one section, we deep-dive into the most commonly performed activity verbs, and the most commonly used tools, as well as their relationships to the activity categories we defined above. This detailed analysis is performed in both contexts of present-day digital systems, and legacy systems pre-dating them. This comparison demonstrates how both generations of these systems and tools are ultimately enabling the same categories of supporting activities following similar patterns. All of this can inform future efforts to define next-generation self-sovereign identity systems, given that the same patterns will likely hold true there.
Patterns of activity
Looking through the economic lens, we can generally organize human activities as hierarchic structures, ultimately meant to support transactions with positive value creation. This can result in the oversimplified yet helpful notion that all sustainable forms of activity directly or indirectly contribute to value creation.
At a high level, transactions generally go through the following stages:
- Establishment of information, identity, and reputation.
- Preparation of resources including objects or relationships for access.
- Acting to establish agreements through personal interaction and resource access. Also completing preparations preceding an upcoming transaction.
- Creating value through completion of a beneficial transaction.
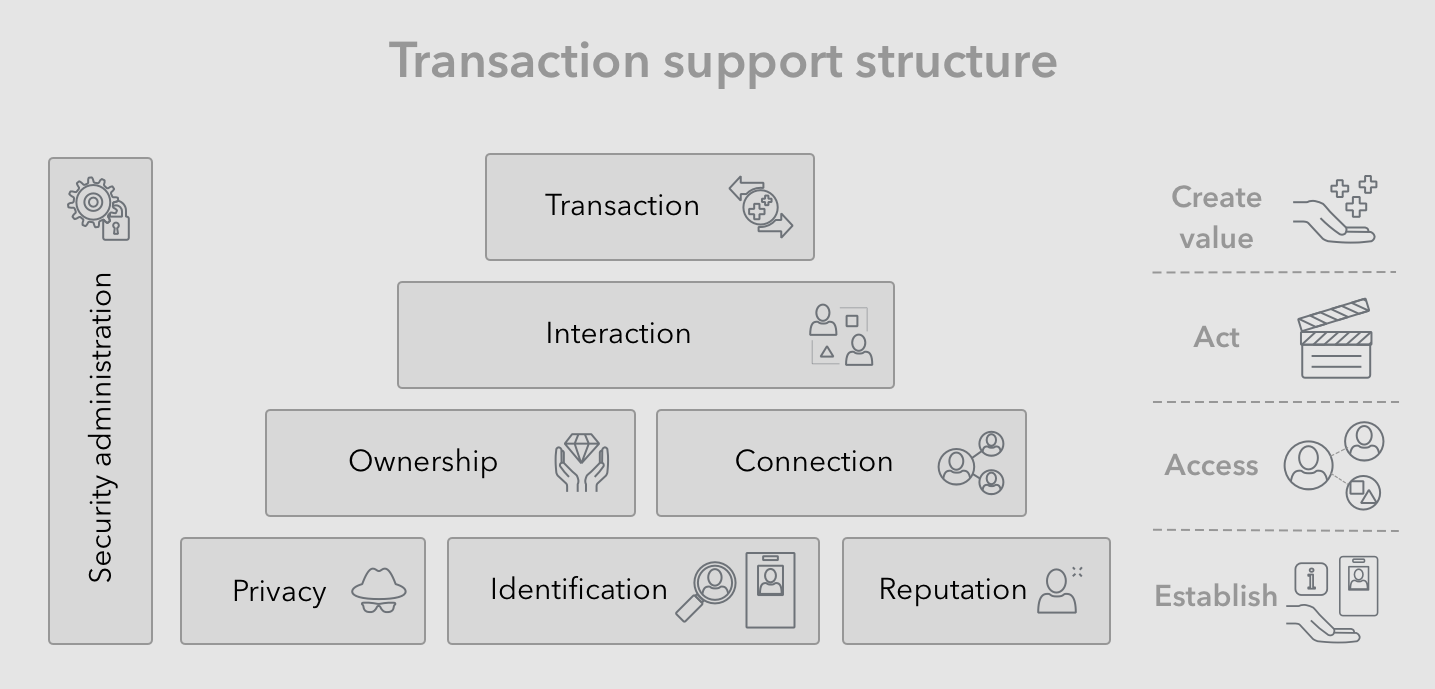
Activities supporting transactions can generally be categorized into the following groups:
- Security administration - All stages and activities may contain additional security and administrative sub-activities, designed to facilitate progress and to mitigate against negative outcomes. For example, a user may have to maintain user name and passwords securely, in order to prevent hacks, fraud, or theft.
- Identification (self) - In multi-party transactions the each party needs to determine the scope and context of their identity and express it to other parties. For example a customer may present their driver’s license.
- Identification (perceived) - Similarly, in multi-party transactions, each party needs to establish the expressed identities of others, verify their identity claims, and assess the level of trust they are willing to extend. For example, a business may ask for and verify a customer’s driver’s license.
- Privacy - Similarly, each party is aware of certain portions of their identity and personal information, that they would not like divulged. They may have to take action to keep said identity information private. For example, a user may set up and use a pseudonymous identity for completing some sensitive transactions.
- Reputation -Similarly, each party involved in a transaction, will have to ensure other parties extend a minimum level of trust. To do this, they can build and express their reputation, through presentation of credentials, or present other promotional information. For example, a job applicant may advertise their education degree, and be required to follow up with sending a copy to employers.
- Connection - As part of preparations for a final transaction, a given party may have to build and prepare a set of relationships, that would help them make progress towards completion of said transaction. For example, a first time customer, may have to establish a new account with businesses, and add their app to their phone.
- Ownership - Again, as part of preparations for a final transaction, a given party may have to store and prepare certain resources, that would help them make progress towards completion of said transaction, the most common of which is monetary value in the form of money. For example, a customer may have to get a checking account and maintain good standing, in order to be able to use it for transactions.
- Interaction - Any given party would have to interact with other parties or resources, that are involved in preparations for a final transaction. Often, part of this activity is establishing agreements between the different parties. For example a buyer may have to contact and communicate with a seller, to establish mutually agreed upon terms, before the final transfer of product and monetary value, and transaction execution.
- Transaction - This represents the final step of above-mentioned activities, resulting in the execution of agreed upon transaction terms, where value is exchanged, and hopefully mutual positive surplus is created. For example, and employee would accepts a job, by signing the employment contract, and following up by providing services as an employee.
There are various examples of large-scale systems created by communities, nations, companies and other large actors, that help reduce costs of economic activity for large numbers of people an organization, in many of the above categories. The public internet is just one notable example of an information system, others are the different types of infrastructure created by national governments, such as highway, telephone and courts infrastructure.
The most common types of large scale systems used to reduce cost of transaction supporting activities are information systems, payment systems, identity systems, communication systems, transportation systems, and legal (governance) systems. Our focus is specifically on identity systems, including their digital and legacy variations.
Identity systems
Much of the activities related to identity systems, or general security efforts that lead up to a final transaction, exist to mitigate or prevent undesirable outcomes in favor of a final and productive outcome. Think reducing the chances of fraud, or outright theft.
Identity systems are commonly used by larger groups of people to optimize social interactions between people and organization. These systems function by securely representing the identities of people, organizations and things, as well as by allowing people to more easily identify, verify, connect, access, and interact by reducing the cost of these activities at scale.
For example, it is common for businesses to use driver’s licenses to identify people and verify their personal information such as name, age, address, etc. Thus, the identity system created by the department of motor vehicles, and supported by the issuance of driver’s licenses, provides the tools for people and businesses to reduce the supporting costs of transactions.
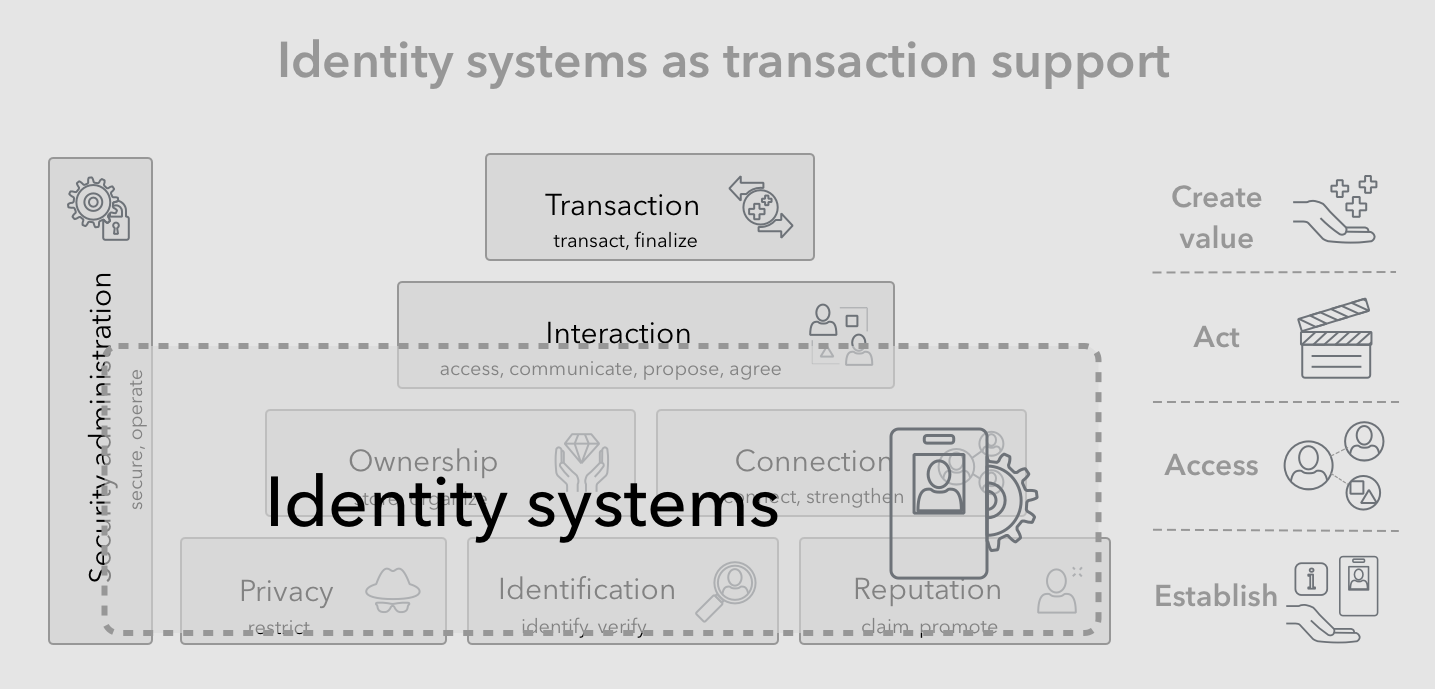
In reality there are multiple layers of these identity systems (such as naming, birth certificates, licenses, passports, employee identification, social networks, etc) working together to create a hybrid identity system, which all people and organizations benefit from. The sheer scale of this hybrid system’s usage and value mean that any improvements in efficiency, has the potential to disrupt current economic activities, as a result of significant reduction of costs. One opportunity that stands out here is the potential to improve efficiency by the combination of digitization and reducing fragmentation.
Activities and tools
We can dive a bit deeper into specific examples of supporting activities and the systems and tools that power them.
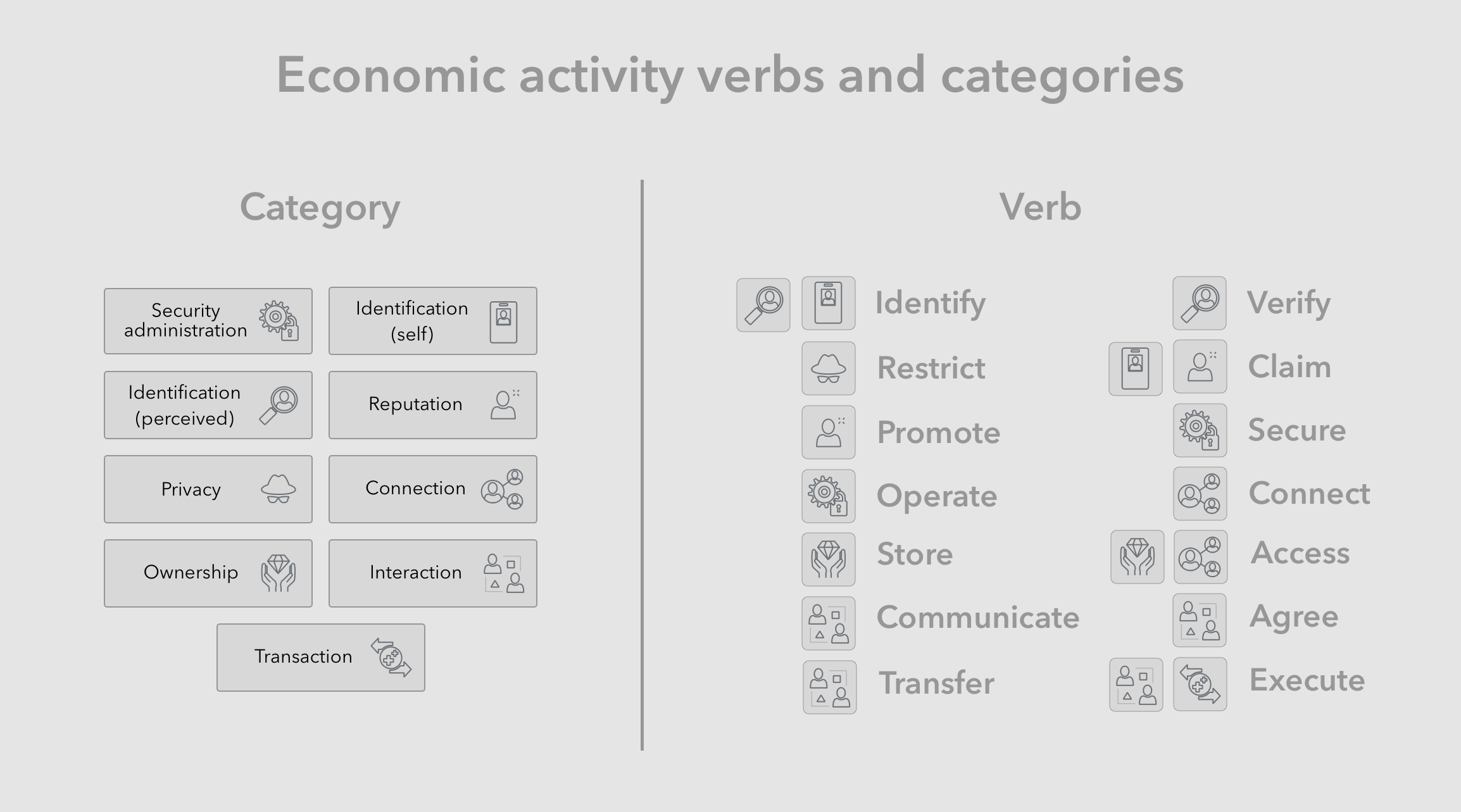
Following are the common supporting activity verbs denoted by their [categories] in brackets:
- Identify [identification (self)] - Is an act of expressing one’s identity information, like the example of presenting another party with your driver’s license.
- Verify [identification (perceived)] - Is an act of verifying an identity presented to you, as well as any accompanied claims. For example, an establishment can verify a patron’s age by reviewing their driver’s licenses and confirming its authenticity.
- Restrict [privacy] - An economic actor can take steps to keep personal information private. For example a customer can explicitly ask a service provider to not record or forget their national identity number.
- Claim [reputation, identification] - Actors make certain claims about their identity when they see it as required or advantageous to completing the transaction. For example, applicants may claim to have a college degree as part of their application and subsequently be required by the employer to prove it with certificates and transcripts.
- Promote [reputation] - To produce leads or to increase the likelihood of deals, economic actors part-take in the act of promoting their personal or business brands. This is essentially the act of highlighting desirable portions of one’s identity information. For example, a job applicant may highlight specific desirable brand associations, experiences, degrees or certificates, with the aim of promoting their personal brand.
- Secure [security administration] - Is an act of making a system or its resources more safe as related to undesirable outcomes such as breach, exploitation, fraud etc. For example having to use strong passwords every time one accesses the system is an act of securing the system and mitigates against unauthorized access by unauthorized actors.
- Operate [security administration] - Any operational act of running a system as expected. For example, users often have to take care of maintenance tasks such as backups, renewing security passwords or certificates. Such actions are always taken with the aim of maintaining the productivity, reliability and security of a system.
- Connect [connection] - The act of connecting with other people and organizations, by forming relationships based on trust and mutual benefit or understanding. Networking activities are great examples of individuals forming new connections which they intent to access and benefit from in the future.
- Store [ownership] - Economic actors take ownership of resources and store them for safe keeping. The act of storing is meant to prevent loss of valuable resources be they due to natural circumstances or malicious actors. For example one can store their valuables in a safe in order to decrease the chances of them being stolen.
- Access [ownership, connection] - This is the act of accessing resources, people or organizations one has a connection with or control over. For example one can invoke and access their contacts from a conference to learn about a new development in the industry. One can similarly access their personal income documents to address a tax inquiry.
- Communicate [interaction] - An act of notifying, requesting or responding to a person or organization one is affiliated with. This is essentially an information-based interaction with a connection. For example one can use email to communicate with a business in cases where their service has not been satisfactory.
- Agree [interaction] - An act of confirming that a proposed agreement is in fact mutually beneficial and should be executed as described. For example signing a commercial deal between two businesses indicates that all parties have agreed to the terms.
- Transfer [interaction] - is the act of moving resources to others that the economic actor has connections with. For example a retail customer can transfer money to a retailer in form of a payment, while the retail transfers merchandise to the customer by shipping it.
- Execute [transaction] - is the act of finalizing the transaction that was agreed upon, meaning that obligations of all parties are realized. For example as part of the retail purchase process, the customer always ends up executing the transaction by confirming their purchase and sending in their payment.
Trends of digital transformation have already resulted in significant changes in many parts of the economic landscape, including in the identity sub-systems we use everyday, even though legacy systems also remain heavily in use. Thus, it is helpful to organize identity system and artifacts into legacy and digital, and observe their form and function, in search of common patterns, and insights and to shape our approach to future-facing solutions.
Legacy artifacts
In the past few centuries, especially following the industrial revolution, human societies have developed and converged on a few common processes, infrastructure systems and tools, related to the identity domain and for the purpose of supporting economic activity. Examples include the systems and norms around the use of identity documentation, such as identification cards and passports. Examples also include legal and financial systems and instruments, such as money, checks and contracts.
Some of the above-mentioned processes and systems have been disrupted or evolved since start of the digital information revolution, however in this section we focus on the systems and tools that remain unchanged by digital technology, thus use of the term “legacy”. We also primarily focus on the artifacts as representative symbols, as opposed to, and in place of their backing systems and processes.
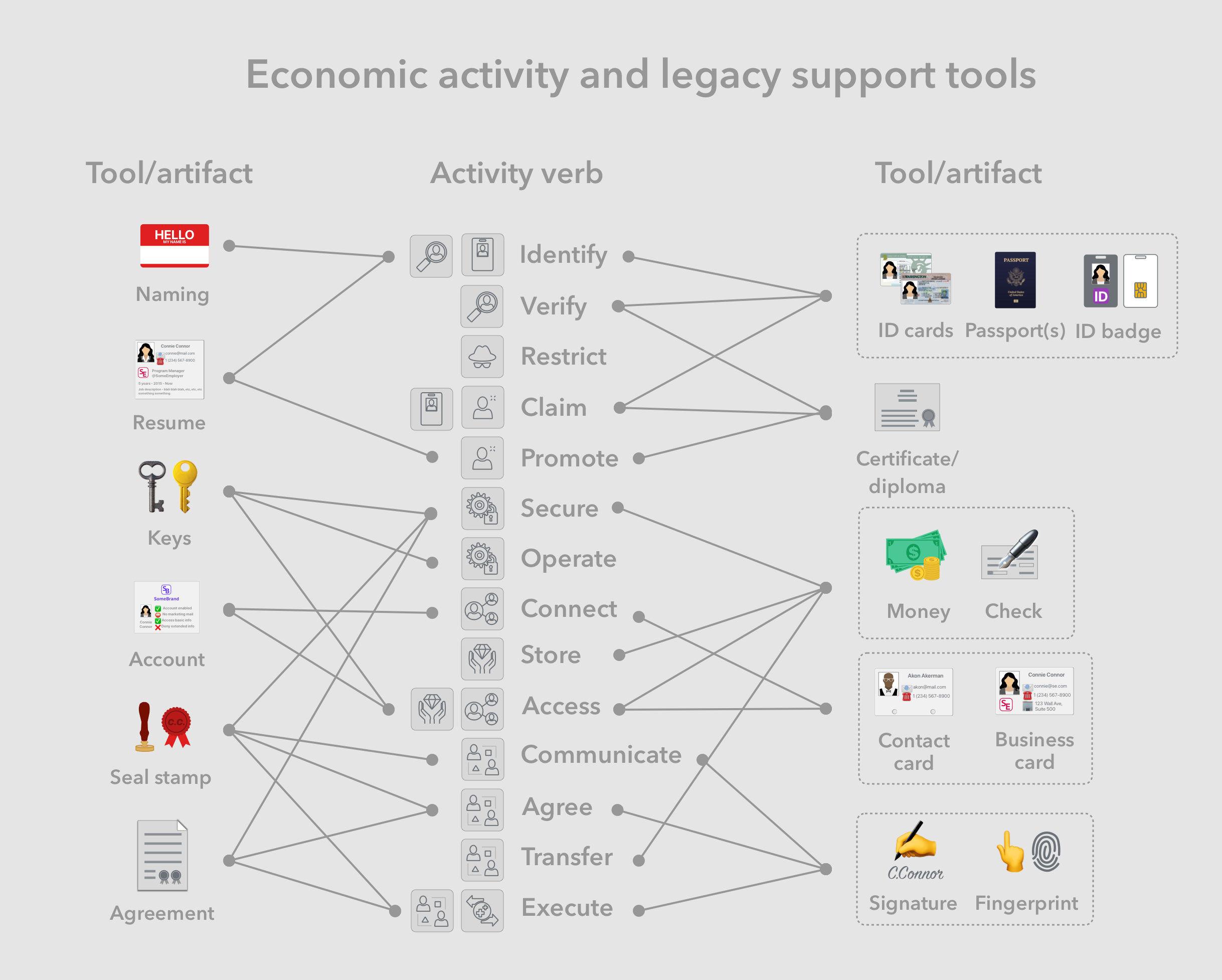
- Identification documentation (Identity cards, badges and passports)- are typically presented by a bearer to a receiver, they are used by bearers to identify themselves and are used by the receivers to verify the identity of the bearer, as well as to authenticate any documented claims. These documents are often issued and supported through a backend system managed by an authority such as the government. For example, drivers licenses are issued by state governments, and are typically required by some businesses to verify the customer’s identity as well as information such as date of birth.
- Resumes (C.V.) - are used in the job application process to document the applicant’s identity, experience and education. The job applicant is identifying themselves as well as promoting their personal brand, and the potential employers are using scanning the contained identity information in their selection process.
- Certificates and diplomas - document one person’s completion of professional training or a set of academic courses sufficient for the issuance of a degree or designation. They are then presented by bearers to other parties that requires proof of that completion. For example, undergraduate students receive a bachelors diploma, which they can present to potential employers during the job application process.
- Keys -Are mechanical instruments with unique physical features that are used to secure and access physical goods, valuables, or controls to a machine. Complementary tools called keychains are used to store, organize and access keys, especially in mobile scenarios.
- Money, checks - Money commonly takes the form of denominated bills or coins, and is used as store of value, medium of exchange and unit of accounting. It is most commonly backed by state treasuries or national banks. Checks are primarily used as a medium of exchange with arbitrary denominations, backed by a given commercial bank. Complementary tools called wallets and checkbooks are used to store, organize and access these artifacts, especially in mobile scenarios.
- Contact cards, business cards - Business cards are primarily used to create, formalize and strengthen business connections, as well to promote an entity’s brand. Contact cards are used to formalize, store, organize and access personal and business connections. Complementary tools such as rolodexes or cardholders are used to store, organize and access these artifacts, especially in mobile scenarios.
- Accounts (at businesses)- Customers often open an account with businesses they have recurring business with, in order for the business to have access to their latest identity, contact and payment information. For example home residents are required to have an account with the electricity company, notify the company of address changes, and keep banking account numbers up to date to facilitate recurring payments.
- Signatures, fingerprints - Physically unique impressions of a person’s handwriting of their name or skin ridges from their fingers are often used as a verifiable sign of that person’s participation or agreement in legal documents. For example, a person’s signature on a legal contract such as a home lease confirms their agreement and binds them to the terms.
- Seal stamps - Stamps or signets are used to both create a unique impression in documents, as well as physically seal documents using wax. Thus they are used as a verifiable sign of a given entity’s participation or agreement in legal documents, and as proof of non-tampering for physical documents.
Digital artifacts
As mentioned, some of the processes and systems in use since the industrial revolution, have been disrupted or have evolved since start of the digital information revolution by taking advantage of digital technology and its efficiencies.
Sometimes these improved systems are digital equivalents of their legacy counterparts, as with the example of digitized voice communication over the same phone infrastructure. At other times these systems are rebuilt on a completely new digital foundation, and present completely new opportunities, such as with the example of the internet and electronic mail. Below, we focus on particular artifacts, as opposed to, and in place of their backing systems and processes.
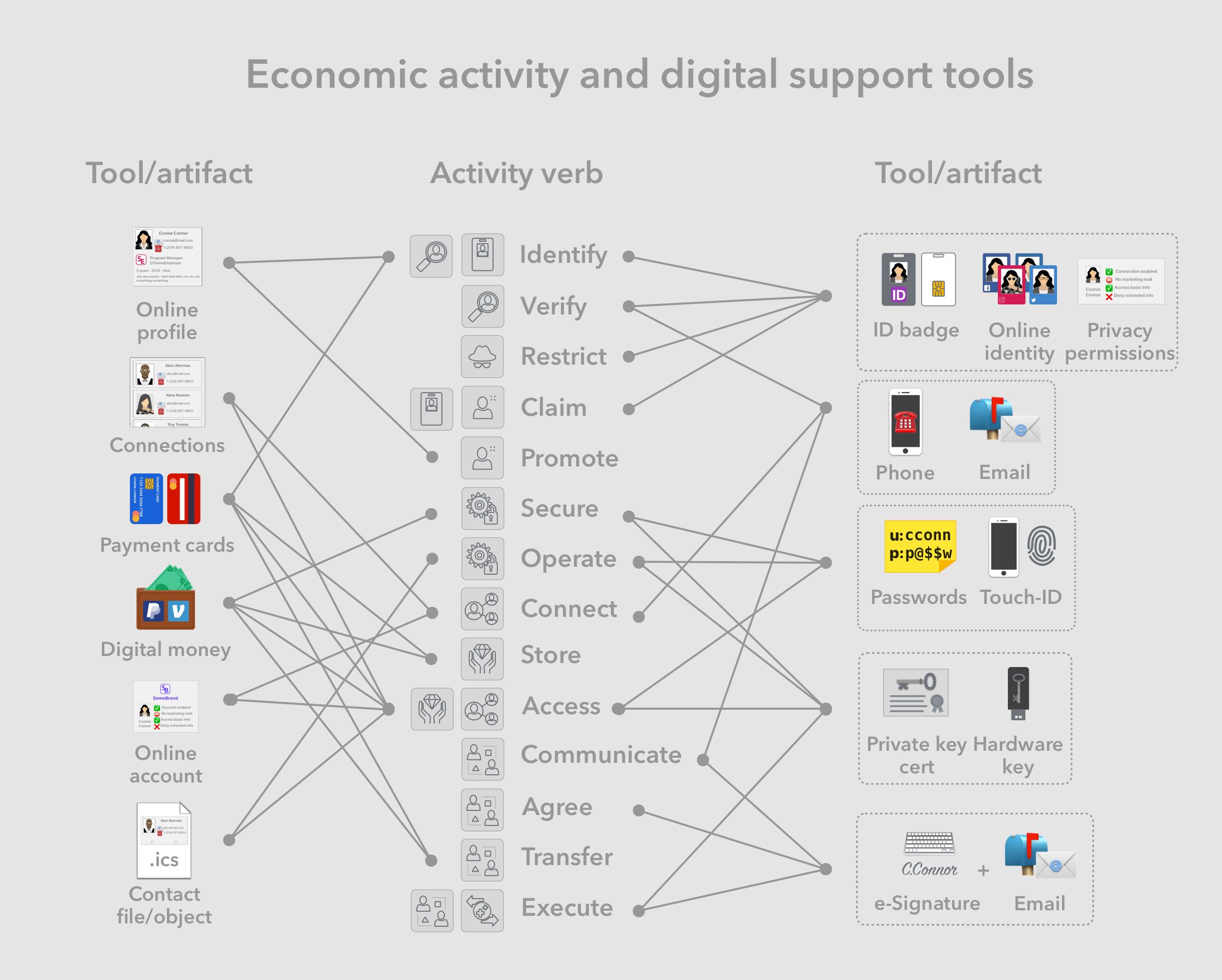
- Online identities - are digital representation of subsets of a person’s multiple identities, often hosted by, and managed through social networks as identity providers. Some of these identity providers also provide the ability to log into external web services, and provide privacy settings for restricting access to certain identity information. For example, a person can use a Facebook identity for social posts, as well as logging into affiliated web services with limited data sharing, while using their LinkedIn identity to represent their professional identity.
- Online profiles - Are expressions of a person’s public identity, published with the help of social networks. They are often used to promote a personal brand in order to increase the chances of forming new productive connections. For example, professionals post their professional profiles on LinkedIn sometimes in place of their business cards or resume, in order to enhance their connections as well as to create new professional opportunities.
- Connections - Are digital representations of a person’s connections with other persons, organizations or things, managed through social networks, or through contact management apps. For example, a person can maintain their list of friends through a social network like LinkedIn, and integrate that with additional identity information stored on their phone contacts app.
- Digital certificates, hardware keys - Private keys are a fundamental building block of cryptographic security systems, and are often used in high security scenarios. Possession of a digital certificate file, and ability to sign data with it, proves one’s control over a given private key. Hardware keys feature additional protection provided by hardware security modules, which are extremely resistant to online exploitation. For example, some developers use digital certificates to sign code before publishing, and some use hardware keys to store the underlying private key, and to sign published code.
- Passwords - are unique combinations of characters, often also accompanied with a unique user name, that allow for secure access into digital system and over digital resources. Complementary tools such as password manager apps are used to store, organize and access passwords in a more efficient manner.
- Online accounts - With the increasing universality of internet access, most businesses have made their customer account systems accessible through the web. In fact it is now the norm for new customers to create and manage an account with said business through their site and mobile app. consumer businesses the existing account systems When signing up for web-services
- Payment cards - Debit and credit cards - Are primarily used by consumers to make payments to retail and commercial businesses in return for products and services. They can also be used to identify and verify the owner and map to other identification documents such as driver licenses. The various flavors of these cards, namely credit, debit, cash, etc, have more to do with the consumer’s credit and payment structure, as opposed to the purchasing process.
- Digital money - PayPal, Venmo, Zelle, etc - Are used by consumers to transfer monetary value to personal and business connections. These payment tools are primarily available through the web and thus are well integrated into web and mobile app infrastructure.
- Contact data files - are digital container for identity information. Any entity, including people and organizations, can share their identity information in this format for easier access. It can also be used by the receiver, as part of a contacts application, to organize, store, access and transfer identity information of connections.
- Email - Primarily used for communication, it has additional uses for identification and verification. Each email user is assigned a unique email address, that can be used to identify them, as well as to verify a person’s control over that email account.
- Phone - Primarily used for communication, it has additional uses for identification and verification. Each email user is assigned a unique phone number, that can be used to identify them, as well as to verify a person’s access to that phone number.
- eSignatures - Are cryptographic artifacts defined within the context of a signing web service, such as docuSign, Adobe sign or others, that verify a person’s agreement on a digital legal document. Combined with complementary tools such as email and smart documents, these can be used to represent legal documents and processes digitally.
Market sizes
Although it is extremely difficult to aggregate and measure the macro value of above-mentioned economic activities on holistically, we can use data from existing sub-markets, especially in the enterprise segment, to get an idea for the magnitude of the greater market for identity systems.
Generally most activities fall within the following markets: 1. Consumer 2. Enterprise 3. Government and institutions. Much of the activity in the Consumer segment is difficult to measure as most products are not priced to reflect real financial values, instead these products are monetized through other means such as advertising, or up-sell to other more valuable services. The government (public sector) segment is somewhat measurable based on some transparency in budgets, but it still does not reflect the more accurate market driven pricing. However enterprise markets are generally more measurable due to a vibrant market ecosystem around offerings.
Let us focus on the enterprise segment, and dig deeper into a few sub-segments for market size estimates. The enterprise identity market is generally divided up into somewhat arbitrary sub-segments such as: Identity access management (IAM), Identity verification, Enterprise authentication (including Multi-factor auth. and Single sign-on (SSO)) as well as a few other related and niche categories such as Device management, Password management, Digital transaction management, Reputation and creditworthiness.
Market size projections exist for at least a few of these categories, and here we consider conservative estimates by looking at minimums of multiple projections. These include: Identity verification estimated to grow to over $15B by 2025, Enterprise authentication to grow to over $17B by 2025, and IAM estimated to grow to over $20B by 2025. There are many activities and sub-segments that are not considered as part of the above markets and estimates, such as the development and operational overhead that will still be incurred by enterprises with their existing custom solutions.
For the consumer segment, we have a few other reference data points that may help measure economic activity. As of 2017 a conservative number for the number of logins per year occurring through the social media identity providers such as Facebook and Google, is over 300B. Other sub-segments that are related but not considered include: Social networking and communication, reputation and creditworthiness, content on social networks, identification documents and verification.
There are market projections from a growing sub-segment of the consumer market, namely password managers, despite the market being largely commoditized by device platform providers such as Google and Apple. Nevertheless the sub-segment is estimated to grow to as much as $2B by 2025. Overall we believe it conservative to estimate the macro identity systems market to be over $200B in real economic value size, however given the difficulties in including and measuring much of the economic activity, we believe it could be easily something over $0.5T.
Conclusion
Looking through the economic lens, identity systems and their corresponding artifacts manifest as tools that enable economic actors to more easily perform productive activities and ultimately create value.
The ongoing trends of digital transformation have not changed the existential need for identity systems and tools that support economic activity. Instead, they have primary contributed to the new digital form of these systems and tools, as well as improvements to their efficiency.
Given their ubiquitous presence across the economy, improvements in the efficiency of identity systems en masse, has the potential to disrupt a large portion of current human economic activity, as a result of significant reductions in costs. Accordingly, one macro opportunity that stands out is the potential to improve economic efficiency by a combination of digitization and fragmentation reduction.